What is SSL and How does it work ?
What is SSL?
SSL (Secure Sockets Layer) is a security protocol that encrypts the data that is transmitted between a web server and a web browser. It ensures that the data transferred between the two is in an unreadable format to anyone who may intercept it. SSL certificates, sometimes called digital certificates, are used to establish an encrypted connection between a browser or user’s computer and a server or website.
SSL uses asymmetric cryptography to initiate the communication which is known as SSL handshake. Most commonly used asymmetric key encryption algorithms include EIGamal, RSA, DSA, Elliptic curve techniques and PKCS.
SSL uses symmetric cryptography using the session key after the initial handshake is done. The most widely used symmetric algorithms are AES-128, AES-192 and AES-256.
How does asymmetric cryptography work?
Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for encryption, then the related private key is used for decryption. If the private key is used for encryption, then the related public key is used for decryption.
The two participants in the asymmetric encryption workflow are the sender and the receiver. Each has its own pair of public and private keys. First, the sender obtains the receiver’s public key. Next, the plaintext message is encrypted by the sender using the receiver’s public key. This creates ciphertext ( encrypted text ). The ciphertext is sent to the receiver, who decrypts it with their private key, returning it to legible plaintext.

Because of the one-way nature of the encryption function, one sender is unable to read the messages of another sender, even though each has the public key of the receiver.
How does symmetric cryptography work ?
In the symmetric cryptography, there is only one key which encrypts and decrypts the data. Both sender and receiver should have this key, which is only known to them.

Data Transfer over SSL
SSL protocol uses asymmetric and symmetric cryptography to transfer data securely. The following figure illustrates the steps of SSL communication:

As you can see in the above figure, SSL communication between the browser and the web server (or any other two systems) is mainly divided into two steps: the SSL handshake and the actual data transfer.
SSL Handshake
The communication over SSL always begins with the SSL handshake. The SSL handshake is an asymmetric cryptography which allows the browser to verify the web server, get the public key and establish a secure connection before the beginning of the actual data transfer.
The following figure illustrates the steps involved in the SSL handshake:
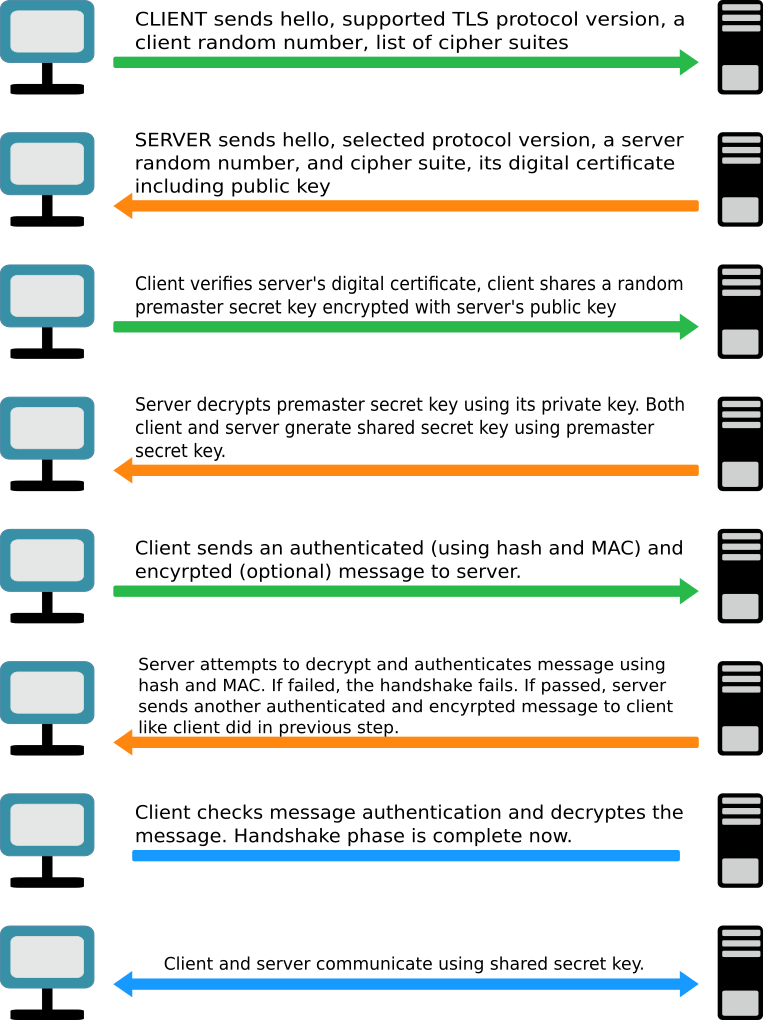
Let’s understand the above steps:
- The client sends a “client hello” message. This includes the client’s SSL version number, cipher settings, session-specific data and other information that the server needs to communicate with the client using SSL.
- The server responds with a “server hello” message. This includes the server’s SSL version number, cipher settings, session-specific data, an SSL certificate with a public key and other information that the client needs to communicate with the server over SSL.
- The client verifies the server’s SSL certificate from CA (Certificate Authority) and authenticates the server. The client creates a new key called the “pre-master key” and sends it to the server encrypted with the server’s public key.
- The server decrypts the pre-master key using its private key. Both the server and client now use the pre-master key and compute a shared secret called the session key (symmetrical encryption key).
- The client sends a test message that’s encrypted with the session key to the server.
- The server receives the message, decrypts it using the session key, and sends an acknowledgement that’s also encrypted using the session key back to the client, requesting to initiate the session.
- The session begins and both the client and server use the session key to encrypt their communication during the rest of the session.
Thus, at the end of the SSL handshake, both the client and the server have a valid session key which they will use to encrypt or decrypt actual data. The public key and the private key will not be used any more after this.
Actual Data Transfer
The client and the server now use a shared session key to encrypt and decrypt actual data and transfer it. This is done using the same session key at both ends and so, it is a symmetric cryptography. The actual SSL data transfer uses symmetric cryptography because it is easy and takes less CPU consumption compared with the asymmetric cryptography.
Thus, SSL fundamentally works using asymmetric cryptography and symmetric cryptography. There are certain infrastructures involved in achieving SSL communication in real life, which are called Public Key Infrastructure.
Public Key Infrastructure
The public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage public key encryption.
PKI includes the following elements:
- Certificate Authority: The authority that authenticates the identity of individuals, computers and other entities.
- Registration Authority: A subordinate CA that issues a certificate on the behalf of root CA for specific uses.
- SSL Certificate: The Data file that includes the public key and other information.
- Certificate Management System: The system which stores, validates and revokes certificates.
